As discussed in the earlier post, in-browser mining is the technique of using visitors computational power (CPU) for mining with or without the consent of users. Mining without the consent of the user is the threat and its called crypto jacking. While working on the recent project I came across that, majority of websites providing free contents are involved in in-browser mining. In this blog post, I will try to throw some light on detection of in-browser mining. I will talk more specific to

1) By inspecting the source code
While working on project of detection of in-browser mining, I came across different facts. I analyzed the mining code and tried to figure out about how it works and how browser can itself be used to detect it.
In Google Chrome:
- On the opened web page, right-click and select
Inspect or press Cltrl+Shift+I - On the inspect sidebar, select Source tab
- I am showing the example of the test website which I used for my project
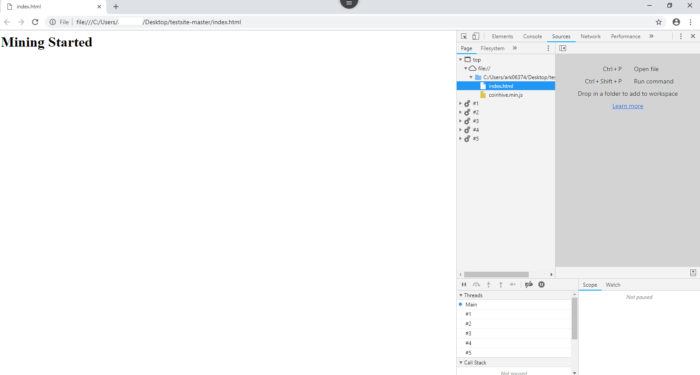
- In the source tab, check if any coinhive.min.js or auth.min.js script is loaded. If yes then you may be the victim of in-browser mining.
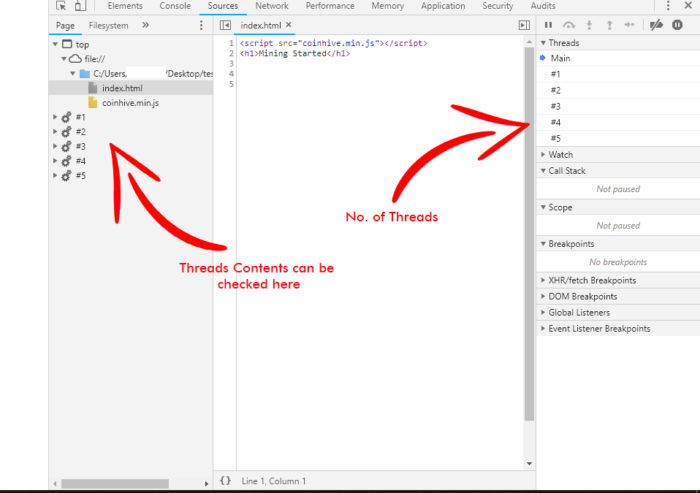
- If you don’t find above scripts and if still, you are suspicious then you can further confirm, by checking a number of threads generated by the webpage. Look out for the threads windows in the same tab. If you find plenty of threads even though the webpage is static, then you may be the
vicitim of in-browser mining.
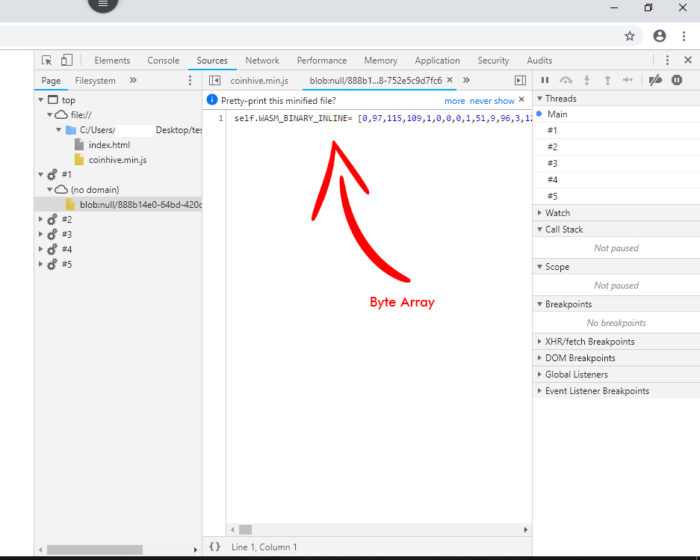
- Further, you can confirm by going through the source code and check for the keywords like miner.start() or auth.min.js or check if you can find the bytecode array. People who don’t know what is bytecode array can just see if something like A = [121, 23, 434, 23] is present in the JavaScript (.js file).
- Please note, that presence of byte code doesn’t imply that its used only for mining. It may also be used for some legitimate work. But if all the above conditions are valid, then you may infer that your CPU is used for in-browser mining.
Note that the in-browser mining doesn’t take place in the mobile. Due to the fact that the mobile’s computation power is not sufficient for in-browser mining. So you don’t need to worry about in-browser mining during browsing on mobile.
2) By using Chrome/Firefox Extensions
There are many chrome extensions available which can used to block the in-browser mining websites. Most of the extensions blocks the blacklisted domains. I am not sure about do they detect the in-browser mining which is done using Wasm. As Wasm is the still the evolving technology, many extension may fail to detect them. Also don’t know about the blacklisted domain database and how frequently it is updated.Some of the well-known extensions are :
- NoCoin: NoCoin is one of the most used chrome extensions for blocking the in-browser mining. NoCoin is open-source and you can find its code on GitHub. Click here to know more.
- minerBlock: minerBlock is my favorite one. It is the chrome extension. It does not just use the traditional approach of blocking the blacklisted domain but also checks for the loaded scrips and kills the suspicious one. Click here to know more.
- NoScripts: NoScript is the Firefox extension. It allows the web pages to load scripts only from trusted domains. Click here to know more.
3) By AntiVirus Softwares
Antiviruses which provides the feature of browsing protection like Norton, QuickHeal etc, can block the mining script. Many antiviruses have blocked the website conhive.com and all the calls made to that website. So installing
Take Away
- Though there are many ways of detection of in-browser mining, the solid method of detection is yet to be invented. My current research project is to develop the tool for detection of in-browser mining using deep learning approach.
- Till then you can stay safe by the methods suggested above.
Thanks for reading!
You may find my completed project details in below slides.